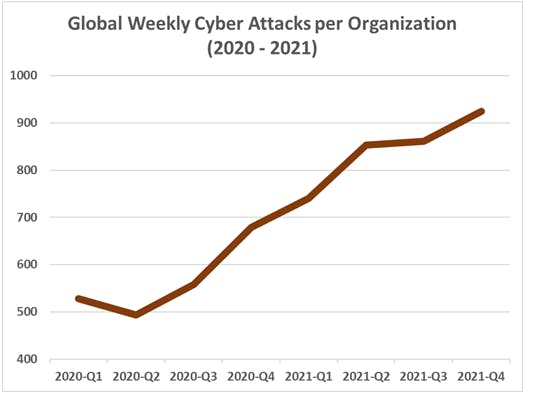
Cyber-attacks have become a global problem for businesses, especially small ones.
It may look like huge companies are the ones that suffer the most from data breaches, but in reality, SMEs have a more challenging time recovering from cyber incidents.
This happens because advanced threats can cause thousands of dollars in damage, and bigger enterprises can recover easier from such losses.
Forty-three percent of businesses that suffer from cyberattacks are small-sized ones.
You won't only suffer from the damage done to your system but also have to pay fines due to data protection laws. These are enough reasons for you to take outsider and insider threats seriously.
Few small businesses are confident they are fully ready and prepared for future attacks. That's why it's essential to get familiar with the nature of cybersecurity incidents and prepare an incident response plan as soon as you can.
Incident response planning can help your team respond quickly if a cyber incident occurs. In this article, we will discuss everything you need to know about incident response processes and the best five tools to help you with that.
This is the second article in our series of articles on incident response. You can read our first article on incident response templates and how to set it up here.
What are incident response tools used for?
Incident response tools help organizations quickly identify and assist in stopping different types of security issues.
Security incidents can be:
- Attempts to gain unauthorized access
- Changes to the system without the owner's knowledge or consent
- Theft of information
- A customer or internal source noticing unusual system behavior
- Virus outbreaks
- The unauthorized use of a system for the processing of data
Incident response tools analyze and address security incidents by gathering information from identity systems, system logs, etc.
That's not all, as they also alert the incident response team to investigate the threat further.
They streamline the incident response process and prevent security teams from performing repetitive tasks manually. Such tools are an important part of the incident response plan of your business.
What is an incident response plan?
An incident response plan is several procedures and tools that your incident response team can use to identify and eliminate cyber incidents.
Incident response plans are needed to ensure that the response processes effectively minimize data breaches and other attacks.
The SANS Institute’s Incident Handlers Handbook states six incident response processes that a security team should undertake to manage a security incident effectively.
Your incident response plan should have all of them below.
1. Preparation
Before reacting to any attack, your incident response team should begin its plan with research.
You need to determine if a policy details how security incidents should be handled. All team members should then become familiar with this policy and its responsibilities.
2. Identification
In this next step of the incident response plan, security teams should be skilled in monitoring and detecting deviations from normal operations in the system.
Then, they should analyze if such deviations represent actual security incidents. If an incident is discovered, response teams should collect additional evidence, decide the type of the threat, and document everything they discover and the actions they took.
3. Containment phase
After the incident response team has identified the security incident, their next goal is to prevent further damage. This includes:
- Short-term containment — It means isolating a network segment that is under attack.
- Long-term containment — This involves temporary fixes to affected systems to allow them to be used in production.
4. Eradication
In this step, the incident response teams identify the root cause of the attack, remove malware from affected systems, and prevent similar future incidents.
Such actions include the replacement of a weak authentication mechanism that has been the entry point for the attack with a stronger one.
5. Recovery
The incident response team now brings affected production systems back online. They decide the time and date to restore operations, and the manners of testing, and then verify and monitor if systems are back to normal.
6. Lessons Learned
This step is performed no later than two weeks after the security incident, so the information is still fresh for the cyber incident response team. All it's left to do now is to complete documentation that couldn't be documented during the process.
Then, the security staff should identify the full scope of the attack, how it was eradicated, what was done to recover the systems, where the response team was effective, and where they require improvement.
Important incident response stats
To better understand cybersecurity trends and the importance of an incident response plan and tools, we will look at some statistics on cybersecurity operations and skills.
80% of security pros find it harder to find people with security skills — Eight in 10 security professionals in a survey of over 336 participants said finding people with security skills had become harder.
Only 20% of practitioners say their SecOps practices are mature enough — One in five respondents in a survey of more than 250 security operations practitioners said their organizations could handle security issues.
94% of security decision-makers take part in collective defense — More than nine in 10 in a survey of 200 security decision-makers claimed their organizations invest in some form of collective defense.
82% of CEOs say they have a high level of cybersecurity knowledge — Eight in 10 CEOs in a study of 263 senior executives claimed to have a high level of knowledge about cybersecurity issues.
5 Best Incident Response Tools
We have chosen the best five tools to help you with your incident response plan. We will talk about their most essential features, their price, positive and negative reviews from users, and how to contact their customer support. We will also include a list of their pros and cons.
The best 5 incident response tools:
- AT&T Cybersecurity
- Sumo Logic
- ManageEngine
- SolarWinds
- Cynet 360
1. AT&T Cybersecurity
AT&T Cybersecurity, which was previously known as AlienVault, is a helpful tool for organizations that lack the capacity or budget to defend themselves against intelligent threats.
It is powered by the latest AlienVault Labs Threat Intelligence and the Open Threat Exchange, the largest crowd-sourced threat intelligence exchange globally.
AT&T Cybersecurity provides all of the essential security controls and is designed to enable any security staff to benefit from results on day one.
It offers intrusion detection, asset discovery, inventory, log management, vulnerability assessment, event correlation, email alerts, compliance checks, etc.
How much does AT&T Cybersecurity cost?
AT&T Cybersecurity offers three packages. The Essentials package starts at $1075 a month and is billed annually. The Standard package starts at $1695 a month and is billed annually. And the premium package starts at $2595 a month, billed annually.
Does AT&T Cybersecurity offer a free trial?
Yes, AT&T Cybersecurity offers a 14-day free trial.
Does AT&T Cybersecurity offer support?
You can contact AT&T Cybersecurity's security support by filing them a ticket in their Success Center or by contacting them via phone.
They have three phone numbers, one for the Americas, one for the UK, and one for Asia-Pacific.
Pros
- Asset management
- Asset discovery
- Intrusion detection
- Covers a wide variety of systems and devices
- Ease of getting sensors up and running
Cons
- Expensive pricing model based on the amount of data
- It requires a considerable amount of time to set up
- The complicated dashboard can overwhelm new users
2. Sumo Logic
Sumo Logic is a log management product that can deal with large amounts of data and has great processing power.
It derives actionable insights within seconds through the ingestion and analysis of application, infrastructure, security, etc.
You can use Sumo Logic to build, run and secure your app and cloud infrastructures. It offers multiple use-cases and gives a refined look into transactions in your platform for all customers.
How much does Sumo Logic cost?
Sumo Logic has five packages, including a free one, but it's limited to 1.5GB a day. You have to pay $3.00 per GB logs with the Essential package. You have to pay $4.00 per GB logs with the Enterprise Operations package. And with the Enterprise Security package, you have to pay $4.25 per GB logs. You will need to contact the sales team for the Enterprise Suite package's price.
Does Sumo Logic offer a free trial?
Yes, Sumo Logic offers a 30-day free trial.
Does Sumo Logic offer support?
Yes, Sumo Logic offers support, but unfortunately, the only way to contact them is by submitting a request on their website.
You can also ask questions to other users on their Community Center or check their Knowledge Base page, which has tips, how-to articles, and frequently asked questions.
Pros
- Enables email alerts based on log information
- Enables users to create dashboards based on events
- The UI is simple and intuitive
Cons
- Dashboard functionality needs improvement
3. ManageEngine

ManageEngine offers IT management solutions to optimize your business processes, and several of them are also solutions for your organization's security.
It helps you protect your data from internal and external threats through security information, identity and access management, endpoint security, network security, etc.
How much does ManageEngine cost?
ManageEngine offers all its products at different prices. But their DataSecurity Plus product, for example, has four pricing packages. The File server auditing plan starts at $745.00 with two file servers per year. The File analysis plan starts at $95.00 with one TB Data per year. The Data leak prevention package starts at $345.00 with 100 workstations per year. And the Data risk assessment package starts at $395.00 with two TB (Data) per year.
Does ManageEngine offer a free trial?
Yes, ManageEngine offers a 30-day free trial.
Does ManageEngine offer support?
Yes, ManageEngine does not only offer customer support, but they also offer many ways to contact them.
You can write them an email or contact them by their US, UK, CN, and Aus phone numbers. You can also submit a query form on their website, explore their help center or engage with their community.
Pros
- Track file creations and modifications
- Track disk space for file systems monitored
- It triggers alerts and helps potential quarantine ransomware
- Helps with reporting for compliance with SOX, HIPAA, FISMA, GDPR, PCI, etc.
Cons
- It is costly compared with the features its competitors offer
- It doesn't allow setting report specifications for risk analysis \
4. SolarWinds

SolarWinds is an IT-management software that offers many products just like ManageEngine. It helps you protect your network, your data, and your systems. SolarWinds tools help customers detect and respond to incidents immediately.
Its IT security products include Access Rights Manager, Security Event Manager, Server Configuration Monitor, Patch Manager, Identity Monitor, Serv-U Managed File Transfer, Serv-U Secured FTP, and Serv-U Gateway.
How much does SolarWinds cost?
Just like ManageEngine, SolarWinds offers its products at different prices. Unfortunately, SolarWinds starts at $2342, the Server Configuration Monitor starts at $942, the Patch Manager starts at $1780, the Serv-U Managed File Transfer begins at $2835 per server, etc.
Does SolarWinds offer a free trial?
Yes, SolarWinds offers a 14-day free trial.
Does SolarWinds offer support?
Yes, SolarWinds lets you contact them in many ways. You can call them at their Americas, EMEA, DACH, or APAC phone numbers. You can also call them on their international toll-free numbers. You can even send them an email or submit a question on their website. They also have a community with more than 150,000 members.
Pros
- It is flexible with various system connectors
- Easy to set up
- The rules are straightforward and pre-configured
- Reduced amount of time spent unlocking accounts
- Great customer service
Cons
- Agent installs in some cases, need manual removal
- If you have an older version of SEM, migrating customers to a new install isn't clear-cut
- The UI is slow to respond after the solution has been running for a while
5. Cynet 360
Cynet 360 is the world's first autonomous breach protection platform that provides integrated capabilities of Next-Generation Antivirus, Network Detection Rules, Endpoint Detection and Response, and User Behavioral Analytics Rules.
It also includes a full set of remediation actions to address infected hosts, attacker-controlled network traffic, malicious files, and compromised user accounts. It makes robust breach protection easy to reach for any organization by eliminating the need for complex multi-product stacks.
How much does Cynet 360 cost?
Unfortunately, Cynet 360 doesn't report the price of its products, but some customers on the internet have admitted that Cynet 360 can cost you $20,000 to $28,000 per year.
Does Cynet 360 offer a free trial?
Yes, Cynet 360 offers a 14-day free trial.
Does Cynet 360 offer support?
Yes, you can contact their 24/7 line by their EU phone number or submit a request on their website, and they will get back to you within 24 hours.
Pros
- It is fast to deploy and needs minimal configuration
- Advanced functionality with hardly any learning curve
- Great level of automation
- It can be used in autonomous mode, and then it automatically prevents malware threats
Cons
- Issues with compatibility
- Unresponsive customer service
- Aggressive roadmap in new functionalities
- Could have greater integration with additional security applications
Conclusion
We hope our article was helpful to you and toughed you everything you need to know about the best tools used for an incident response process. If you want to read more about this topic and discover our curated list of incident response templates, check out this article.
We started this article by explaining how dangerous it is for a small business when a security incident occurs. Then, we explained what tools for incident response are used for, what incident response plans are, and the steps you should take.
The last part was our list made up of the top 5 tools for an incident response plan. We explained the most important features of each tool, ways to contact their customer support, their price and if they offer a free trial or not, their positive and negative reviews, and a list of their pros and cons.
FAQ
What are the tools for incident response?
Incident response tools help your business identify threats and assist in stopping them. They can help you with attempts to gain unauthorized access, unauthorized use of your system, theft of information, viral outbreaks, etc.
What is the most important step in an incident response plan?
The most important step in an incident response plan is preparation. It is the most crucial phase for your organization because it ensures that each team member is properly trained for their incident response roles and responsibilities.
What are the six phases of incident response?
A security team should undertake six steps in an incident response process. These are Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned.

